Route 53 public hosted zone, custom domains & reverse proxy
During my learning on Route 53, I noticed a domain name that is suitable for me was still available and at a very affordable price. After evaluation, I've decided to purchase the domain as it can provide multiple essential functions for me.
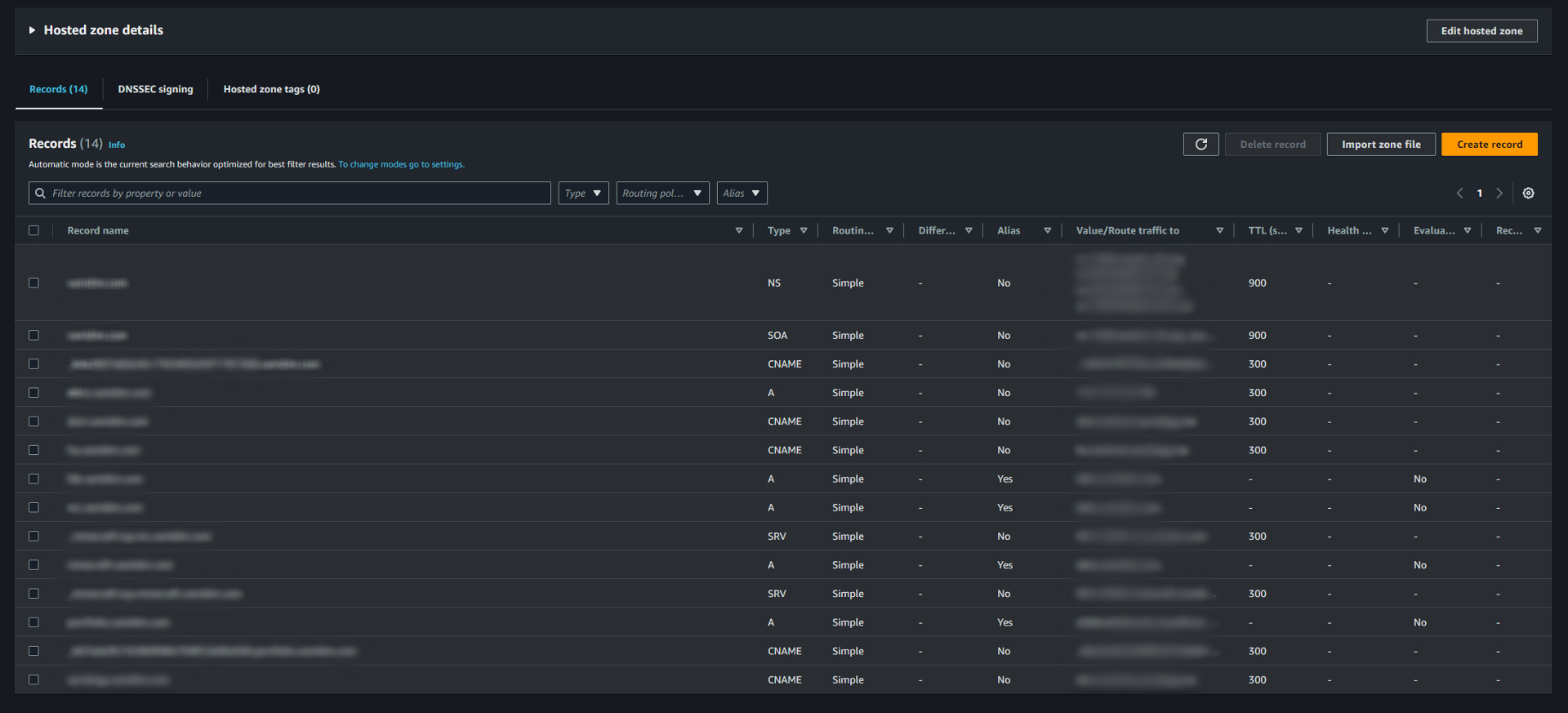
I've then created a public hosted zone on Route 53 by using the domain I've purchased. And created multiple records that serve different functions.
The first thing I did was to create a Lambda function and connect it to my Synology NAS's DDNS feature using the custom provider option. The NAS will then automatically call the lambda function everytime there is a change on my home router's public ip or every 24 hours, this is essential for a few other subdomains on Route 53 records that I've created, since they are hosted on my local network. I then created port forwarding rules on my router for those subdomains' traffic to be pointing to the right local devices. I've also included the guide for custom DDNS at the end of the page, credited to Richard for creating the guide.
I've planned to create multiple subdomains that serve different purposes. The first subdomain is for this portfolio website that I am hosting on AWS as well, you can read more about it from here.
The second subdomain I've created is for remote access to my synology nas's DSM interface, although Synology did provide inhouse DDNs option, but I have felt the url is harder to remember, and have different domain that serves different synology applications, for example xx.synology.me and xx.quickconnect.to for the DSM interface and Synology Drive. So I've created multiple CNAME records pointing to respected synology applications directly.
Third subdomain is also pointing to my synology NAS and using CNAME record, but it does not work directly, as this subdomain is pointing to the Home Assistant instance that I hosted in the Synology's Virtual Machine Manager. It requires me to set up a reverse proxy on the DSM control panel and also configure the correct CIDR block in the home assistant to allow inbound traffic from outside the environment. You read more about the home assistant project from here, and the Synology project here.
The fourth subdomain is unique to other records as it uses the SRV type. This subdomain is pointing to my Minecraft game server that I hosted on my main pc, and the game requires a specific port to be mentioned for others to join my server, but it is hard to remember the specific port needed, as it changes from server to server. So my solution is to create an alias type A record that pointing to my DDNS record, then directly include the port information using a separate SRV record, and when others try to join my game server, they will only need to enter my subdomain address which is basically the name of the server plus my domain name, eg. mc.example.com. A little side note, to prevent scrapers and bots, the servers are whitelisted for better security.
One other subdomain I've created is for my HIKVision NVR, which initially supported first-party DDNS services for external access to the video feeds, but then later being discontinued. And my option was using free DDNS providers like No-IP, but that requires me to renew my record every month, which can be annoying, so I end up setting up my own DDNS with Route 53 and Synology NAS that I mentioned earlier, which leads to no maintenance in the future, while still providing the same function that allows me to stream my NVR video feeds over the internet securely.
Credits for some setup guides:
DDNS with AWS Lambda and Route53: DDNS
with AWS Lambda and Route53
Synology Reverse Proxy: SYNOLOGY REVERSE PROXY
Project information
- Category: Cloud, Network, System Integration
- Project date: 5/1/2024 (last-modified)
- Project URL: -
- Tools: AWS Route 53, AWS ACM, Lambda, Synology NAS
- Technique: Public Domains, Network Routing, Reverse Proxy, REST API, DDNS